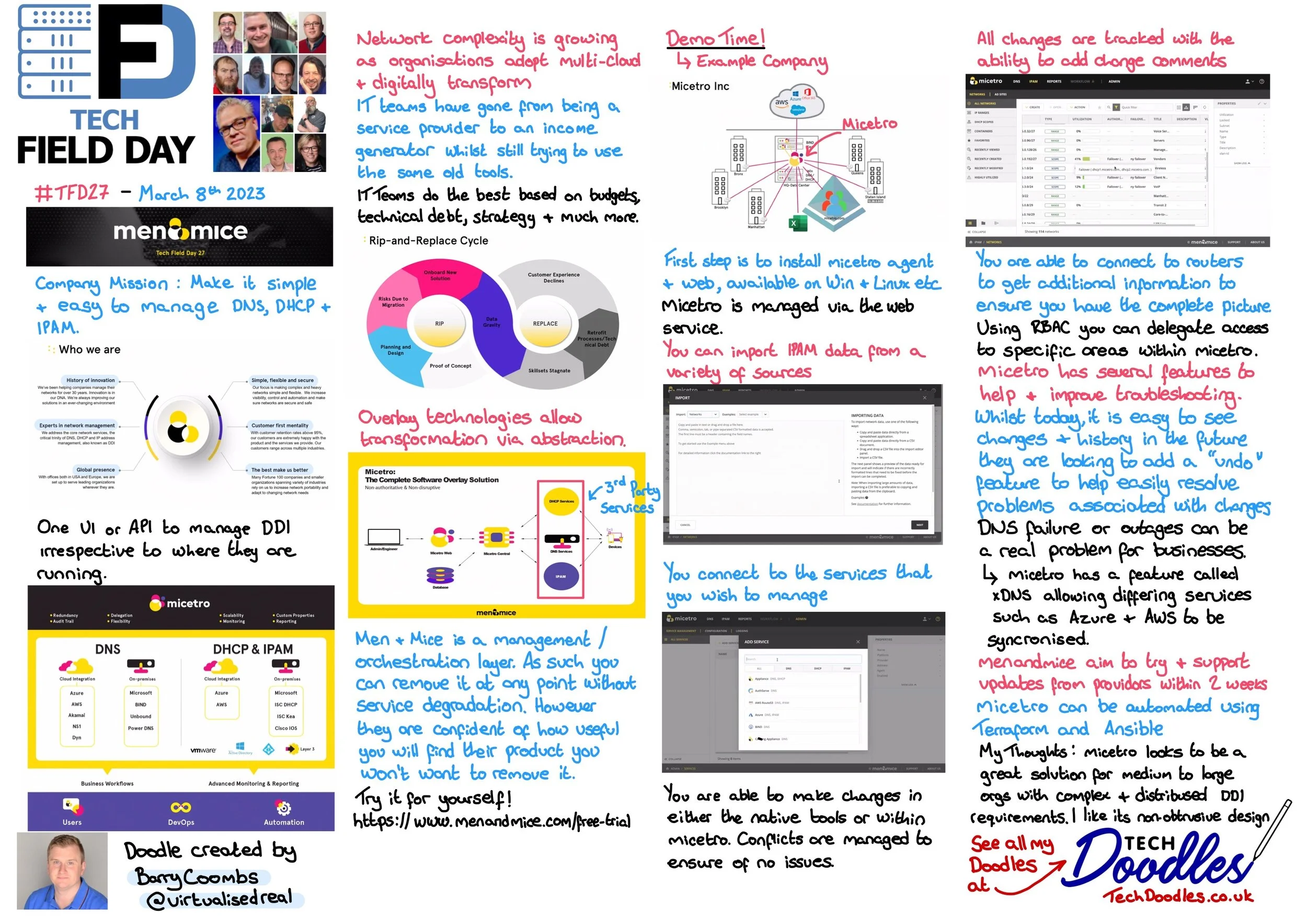
During VMware Explore 2024 in Barcelona, we had the privilege of sitting down with Umesh Mahajan, Vice President and General Manager of Broadcom’s Application Networking and Security (ANS) Division. Umesh’s passion for the ANS portfolio was palpable as he discussed its mission, the evolving landscape of security challenges, and how Broadcom is positioning VMware's offerings to address them.
We posed five key questions during the interview, each shedding light on Broadcom’s vision and VMware’s approach to innovation in this critical space. Below, we’ve highlighted some of the standout points, but we highly recommend watching the full video for Umesh’s detailed insights. You can find the video embedded below!
Key Takeaways from the Interview
The Vision Behind ANS
Umesh began by outlining ANS’s mission: to provide seamless security and load balancing solutions tightly integrated with VMware Cloud Foundation (VCF). Broadcom is focused on delivering advanced services that are as easy to deploy as they are powerful. In Umesh’s words, VMware aims to create solutions that “just click in” like adding features to a Tesla – simple, intuitive, and ready to use.Industry Trends and Challenges
From ransomware attacks to increasing complexity in security infrastructure, the stakes for businesses are higher than ever. Umesh highlighted how frequent and sophisticated attacks, particularly on financial institutions, have underscored the need for best-of-breed security and load balancing solutions. VMware’s approach is to make these tools accessible and scalable for businesses of all sizes, providing both protection and recovery capabilities in one unified stack.Key Announcements and Licensing Simplification
Broadcom’s acquisition of VMware has brought significant changes to how ANS products are packaged and licensed. VMware now offers just three key SKUs: one for Avi load balancing and two for security (firewall and advanced threat protection). These SKUs have been streamlined to reduce complexity and ensure seamless integration with VMware Cloud Foundation (VCF).However, these products are now positioned as add-ons to VCF, meaning they are optional but essential for customers deploying VCF. As Umesh explained, organisations need robust security and load balancing capabilities to complete their VCF deployments, making these Advanced Services critical for operational success. Broadcom’s goal is to simplify the consumption and deployment of these services, ensuring customers can get up and running quickly with minimal friction.
Introducing Security Scoring and Co-Pilots
A standout moment was Umesh’s discussion of security scoring, a feature in development that will help organisations gauge their security posture at a glance. Similar to Microsoft’s approach, the security score will highlight areas of vulnerability, empowering businesses to make informed decisions. Additionally, VMware’s investment in AI-driven Co-Pilots promises to simplify security operations by providing actionable insights in real time.The Road Ahead for ANS
Broadcom’s focus is clear: delivering scalable, best-of-breed products that integrate seamlessly with VMware’s ecosystem. Whether through automation, AI-driven insights, or enhanced recovery capabilities, ANS is committed to simplifying the way businesses secure and optimise their private cloud environments.
Why Watch the Interview?
For anyone interested in VMware’s evolving approach to networking and security. Umesh not only outlines how ANS is addressing today’s challenges but also shares his vision for a simplified, integrated future. From ransomware protection to AI-powered Co-Pilots, there’s a lot to unpack.
Don’t miss this opportunity to hear directly from the leader shaping the future of VMware’s security and networking portfolio. Click below to watch the full interview:
Final Thoughts: Simplifying Security for a Complex World
As Umesh said, security doesn’t need to be overwhelming. By delivering intuitive solutions and minimising complexity, VMware and Broadcom are equipping businesses to handle today’s challenges while preparing for tomorrow’s. Whether you’re a long-time VMware customer or exploring their solutions for the first time, this interview offers valuable insights into how VMware’s Application Networking and Security Division is leading the way.
What do you think of VMware’s approach to security and networking? Let us know in the comments below!